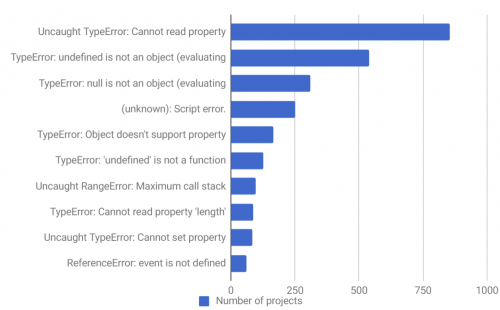
Here’s the list of “Top 10 JavaScript errors from 1000+ projects (and how to avoid them)“. The list is not surprising at all, but still serves as a good reminder on how write better code in JavaScript.
Month: February 2018
The most dangerous word in software development
I think this article – The Most Dangerous Word In Software Development – hits the nail on the head.
“Just” implies that all of the thinking behind a feature or system has been done. Even worse, it implies that all of the decisions that will have to be made in the course of development have already been discovered—and that’s never the case.
Every time somebody asks for “just” this little thing or that little thing, I ask them to “just describe it”, or “just answer a few questions”, or “just pay for it”. Somehow, it never turns up as easy and simple in the opposite direction.
Microservices Architecture : Best Practices
The other day I came across this article: “Microservices Architecture: All the Best Practices You Need to Know“. There’s been a lot said and written about the microservices architectures around the web. But I like this article in particular, because it paints a more realistic picture, in my opinion. Big parts of it are covering the “why?” part of the whole conversation, and it presents a balanced view of pros and cons, as well as several approaches to solving the problems.
This is very refreshing after tonnes of “Microservices are amazing, and are the best thing since sliced bread” and “Microservices is nothing but hype and bubble” coverage out there.
Tsiknopempti
Encrypt MySQL data using AES technique
I came across this blog post from a while back, which demonstrates how to use AES encryption for the data in MySQL database.
INSERT into user (first_name, address) VALUES (AES_ENCRYPT('Obama', 'usa2010'),AES_ENCRYPT('Obama', 'usa2010'));
SELECT AES_DECRYPT(first_name, 'usa2010'), AES_DECRYPT(address, 'usa2010') from user;
This seems rather easy and straightforward (apart from a little calculation one needs to do for the VARBINARY field types). The only thing that I’m concerned about is whether the encryption keys will be visible in the MySQL process list (as in “SHOW FULL PROCESSLIST“).