We had an interesting issue to debug at work today. One of the screens in our application features a form with a whole lot of checkboxes. It’s in the access control module, where the administrator of the system can manage user permissions for each module of the system. Here’s the screenshot just to give you an idea.
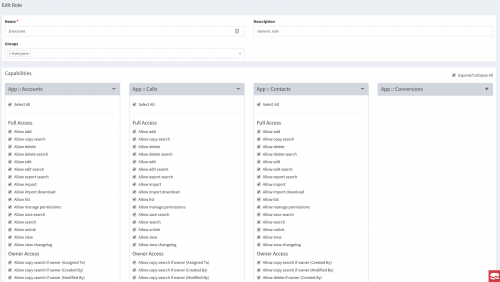
This is not the pretties user interface (yet), but it sort of works. Every module can be expanded or collapsed, and inside each modules all checkboxes can be checked and unchecked easily.
The problem that we had wasn’t user interface related. It was something else. The number of modules and permission checkboxes varies from system to system. This is based on each particular system setup. Now, on some of these systems, it was reported that some permissions are not being saved.
The problem is not new, but it was slowly escalating with more and more clients reporting it. So, today we dived into it and found the cause of it. Since PHP 5.3.9 there is a new runtime configuration setting: max_input_vars, with default value of 1.000:
max_input_varsinteger
How many input variables may be accepted (limit is applied to $_GET, $_POST and $_COOKIE superglobal separately). Use of this directive mitigates the possibility of denial of service attacks which use hash collisions. If there are more input variables than specified by this directive, an E_WARNING is issued, and further input variables are truncated from the request.
So, on the systems, where the form contains more than a thousand checkboxes, PHP was only bringing in the first thousand and skipping the rest, causing not all permissions being saved properly.
Increasing the value in runtime configuration is one way to solve it. But since we have a rather dynamic system and don’t always control the runtime configuration (client hosting), we opted for a different solution. As per this StackOverflow thread, it’s a much more future-proof solution to combine the values into a single field. Either simple concatenate, or JSON-encode the values on form submit, and send them all as a single field value. Then just split or JSON-decode on the server before processing and you are done.
P.S.: The extra bit that made the troubleshooting so much more difficult was that for some reason we were not seeing the PHP warning in logs.