 One of the greatest things about the Amazon AWS services is that they save a tonne of time on the reinventing the wheel. There are numerous technologies out there and nobody has the time to dive deep, learn, and try all of them. Amazon AWS often provides ready-made templates and configurations for people who just want to try a technology or a tool, without investing too much time (and money) into figuring out all the options and tweaks.
One of the greatest things about the Amazon AWS services is that they save a tonne of time on the reinventing the wheel. There are numerous technologies out there and nobody has the time to dive deep, learn, and try all of them. Amazon AWS often provides ready-made templates and configurations for people who just want to try a technology or a tool, without investing too much time (and money) into figuring out all the options and tweaks.
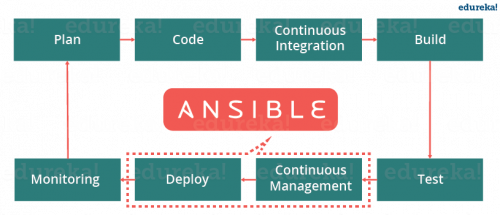
“Get Started with Blockchain Using the new AWS Blockchain Templates” is one example of such predefined and pre-configured setup, for those who want to play around with Blockchain. Just think of how much time it would have taken somebody who just wants to spin up their own Etherium network with some basic tools and services just to check the technology out. With the predefined templates you can be up and running in minutes, and, once you are comfortable, you can spend more time rebuilding the whole thing, configuring and tweaking everything.