Johannes Weber, a networking and security professional, has done something really cool while preparing for his CCNP SWITCH exam. He has built a lab with some networking equipment, configured it all, and captured network traffic, featuring a variety of level 2 and 3 protocols. He has published his setup, the captured traffic, and a variety of challenges, that helped him to prepare, and which can help others.
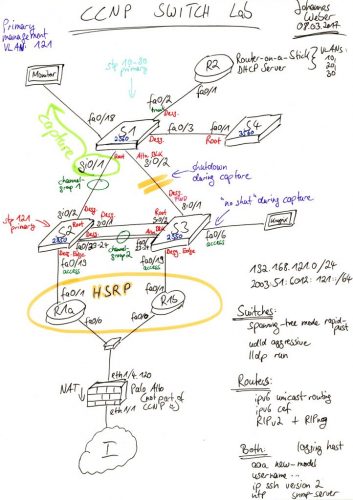
While preparing for my CCNP SWITCH exam I built a laboratory with 4 switches, 3 routers and 2 workstations in order to test almost all layer 2/3 protocols that are related to network management traffic. And because “PCAP or it didn’t happen” I captured 22 of these protocols to further investigate them with Wireshark. Oh oh, I remember the good old times where I merely used unmanaged layer 2 switches. 😉
In this blogpost I am publishing the captured pcap file with all of these 22 protocols. I am further listing 45 CHALLENGES as an exercise for the reader. Feel free to download the pcap and to test your protocol skills with Wireshark! Use the comment section below for posting your answers.
Of course I am running my lab fully dual-stacked, i.e., with IPv6 and legacy IP.
I think these are great for several reasons:
- A feature-rich and complete networking setup, which is not easily available to everyone.
- A fixed set of data (captured network traffic).
- Plenty of very specific, testable, and verifiable questions.
- Overall, very helpful resource from an experience professional, for anybody who wants to know about networks.
- Overall, a great set of questions and challenges for those interviewing networking candidates.
The lab setup includes the following:
- 1x Cisco Catalyst 2960, (C2960-LANBASEK9-M), Version 15.0(2)SE9
- 2x Cisco Catalyst 2950, (C2950-I6K2L2Q4-M), Version 12.1(22)EA14
- 1x Cisco Catalast 3560, (C3560-IPSERVICESK9-M), Version 12.2(55)SE10
- 3x Cisco Router 2811, (C2800NM-ADVENTERPRISEK9-M), Version 15.1(4)M9
- 2x old Notebooks, Dell or somewhat, running either Ubuntu or Knoppix Linux
Personally, I am not very involved with networks these days. But even for more me the above setup serves as a reminder of how complex underlying technology infrastructure has got in recent years – hardware, software, protocols, and all.