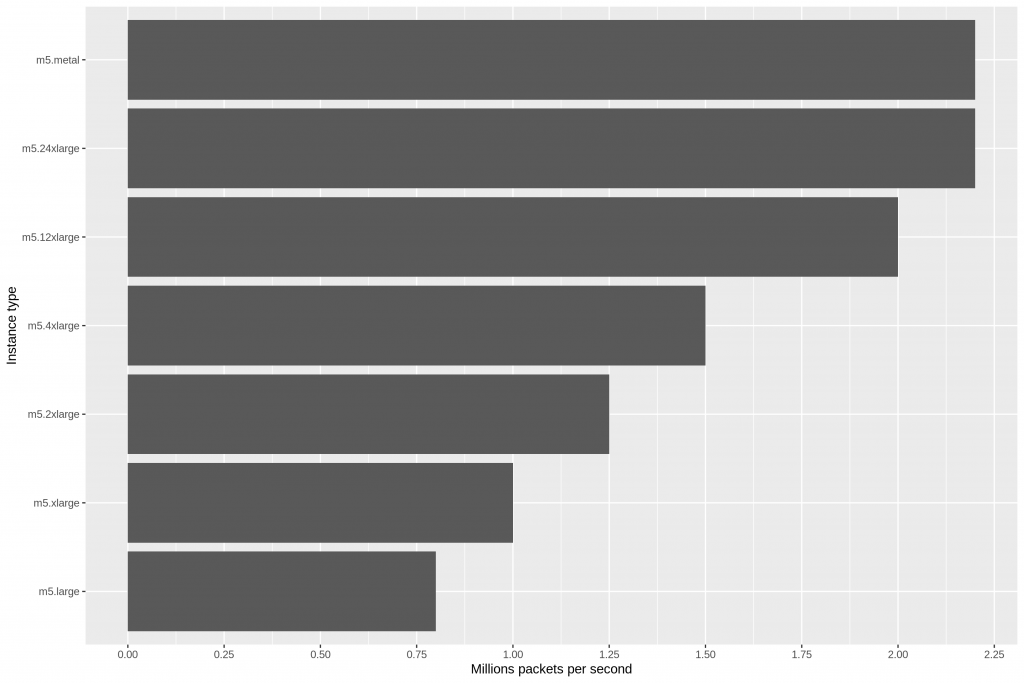
The other day I came across this fun read – DNSFS. Store your files in others DNS resolver caches. And this bit in the article really cracked me up:
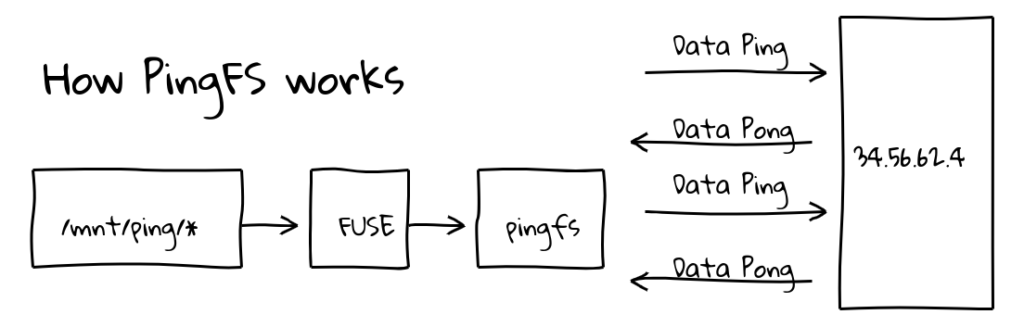
This is not the first time something like this has been done, Erik Ekman made PingFS, a file system that stores data in the internet itself .
This works because inside every ping packet is a section of data that must be sent back to the system that sent the ping, called the data payload.
Because you can put up to 1400-ish bytes in this payload, and pings take time to come back, you can use the speed of light in fiber as actual storage.
Now obviously this is not a great idea for long term data storage, since you have to keep transmitting and receiving the same packets over and over again, plus the internet gives no promise that the packet won’t be dropped at any time, and if that happens then the data is lost.
However. DNS has caches. It has caches everywhere.
Obviously, neither DNSFS, nor PingFS should be used for anything serious, but both are excellent experiments, demonstrating the flexibility of the TCP/IP and thinking outside the box.