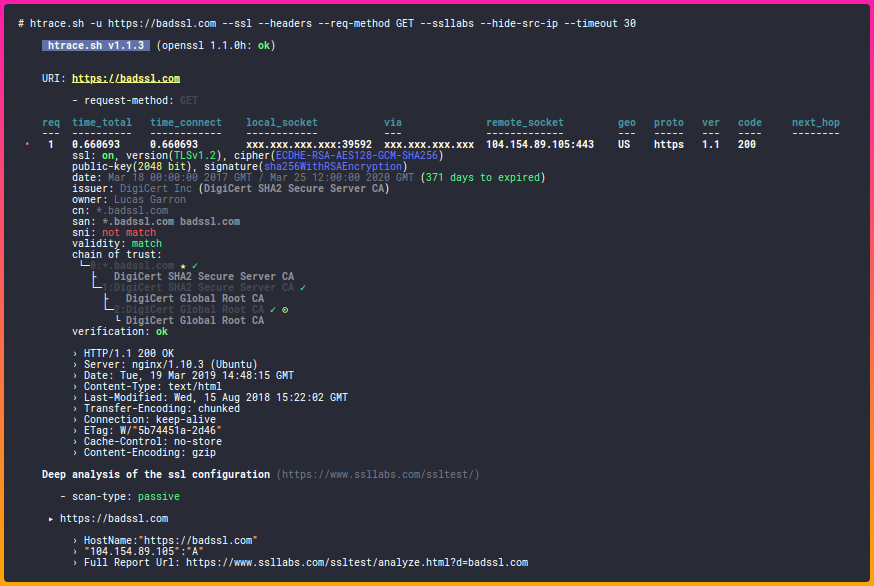
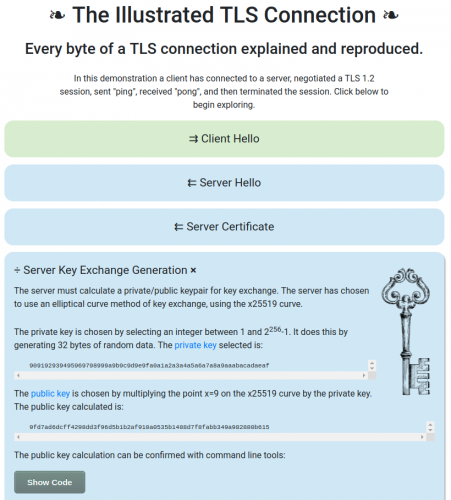
“How HTTPS Works in 10 Minutes” is a simple, high-level overview of how HTTPS works. It doesn’t dive into too much detail or heavy math. But it does cover the main stages of how the connection is established, verified, and encrypted. These are the stages that are covered:
- You go to an HTTPS website via your browser
- The Client says “Hello”
- The Server says “Hello”
- The Client makes sure the SSL certificate is legitimate
- The Client gets the public key from the SSL certificate
- The Client uses the public key to make more random bytes
- The Client and Server make session keys
- The Client and Server compare session keys
- If the session keys match, game on