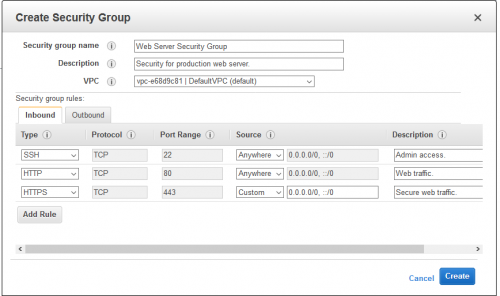
AWS Blog lets us know that Amazon has finally implemented one of the most useful features ever – descriptions on Security Groups rules. Previously, one could provide a description to the Security Group only, for example: “Proxy Server Access”. Which wasn’t very useful, as it was almost obvious. But now one can add a description to every rule inside the Security Group. So when you have a Security Group with a bunch of IP address ranges, you can now describe each one of them. For example: “HQ Office”, “UK Office”, “Boss At Home”, etc.
Year: 2017
Qobo Nicosia Office
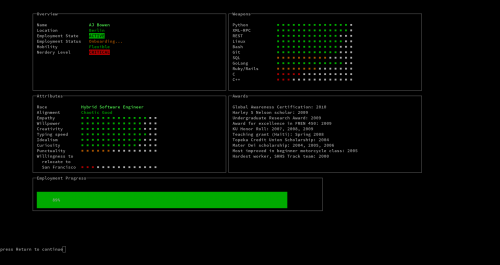
The coolest tech CV ever
This TravisCI blog post welcomes AJ to the team. In it, there is a bit that caught my attention (except, of course, the one about bra burning):
If you’re so inclined, you can follow her on Twitter or run curl cv.soulshake.net.
Wait a second … A what? curl for the CV? I had to try it out. Here’s an even better way, for reading all the slides:
p=1; while [ $p -lt 9 ]; do curl -N cv.soulshake.net/$((p++)); read; done
Oh. My. God. Lo and behold, this is the coolest tech CV I’ve ever seen. Ever. Period. TravisCI is so lucky to have her!
P.S.: If you are interested in how this was done, here a couple of blog posts – one and two.
CakePHP with NightwatchJS on Travis CI
My colleague Andrey Vystavkin has been setting up a testing environment for our CakePHP projects recently. We had one before, of course, using PHPUnit. But this time we wanted to add Google Chrome headless browser with some form of JavaScript test suite, so that we could cover functional tests and a bit of front-end. Andrey described the configuration of NightwatchJS on TravisCI in this blog post. If you are more of a “show me the code on GitHub” person, have a look at this Pull Request (still work in progress) on our project-template-cakephp project.
Once we are happy with the TravisCI configuration, we’ll be bringing this setup to our BitBucket Pipelines environment as well.
The setup is also based around CakePHP framework, but it’s easy enough to adopt it to any other framework, PHP or not.
The end of CSRF?
“The end of CSRF?” blog post talks about the new feature coming to browsers – SameSite cookie enforcement, which will help in getting rid of Cross-Site Request Forgery (CSRF) attacks. Too bad this is currently only supported by Google Chrome (both desktop and mobile), and Opera. But I’m sure it’s coming soon to the rest of the browsers.
Update: It looks like the above blog post is almost a copy of this blog post, which has a number of useful comments. Including this one, which links to a variety of projects and programming languages bug trackers requesting the support of the SameSite cookie feature. Also, it looks like SameSite cookie is superseded by the Cookie Prefix solution, proposed by Google.