Docker Blog is introducing the Moby Project:
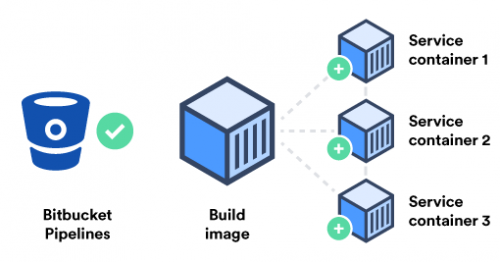
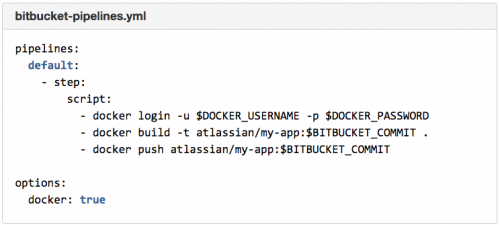
The Moby Project is a new open-source project to advance the software containerization movement and help the ecosystem take containers mainstream. It provides a library of components, a framework for assembling them into custom container-based systems and a place for all container enthusiasts to experiment and exchange ideas.
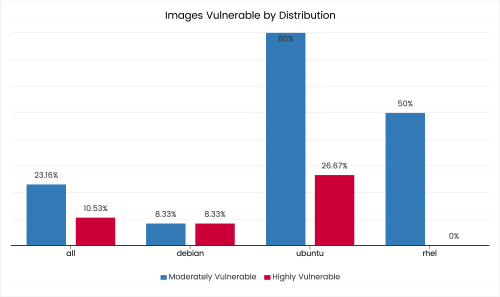
This just had to happen, given the nature of the Open Source and the importance of the container technology for the modern infrastructure.