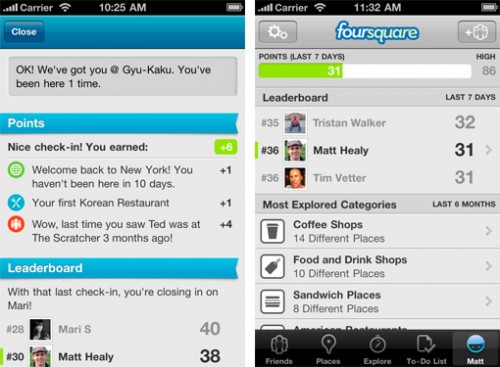
Foursquare – an awesome location services that I use way more than I should – announces the release of Version 3. They have a lengthy blog post explaining their reasons, goals, and changes. And I have to say that it’s exciting. I was slightly worried that they might give up given the Google Latitude check-ins competition, but apparently they are not. Good for them! Anyways, my phone still runs Android 2.1, so the newer Latitude is not available to me. But the new Foursquare is. And there is plenty of new fun, including leaderboards and Explore.
Category: Technology
I work in technology sector. And I do round a clock, not only from 9 to 5. It is my bread and butter, it is my hobby, it is the fascination of my life. And with the current rate of change particular in information technology (IT), there is always something new to learn, to try, to talk about. I often post news, thoughts, and reviews. And when I do, this is the category I use.
chmod text modes
I came across this blog post which praises text modes for /bin/chmod.
There are two ways you can change file permissions in Unix – one is using
chmod‘s symbolic (text) modes (likechmod ug+x file), the other is using the octal modes (likechmod 0660 file). It turns out that symbolic modes are more powerful because you can mask out the permission bits you want to change! Octal permission modes are absolute and can’t be used to change individual bits. Octal modes are also sometimes called absolute because of that.
I have to agree, they are superior. However I feel like the article needs more examples. So here we go.
Use “u” for user, “g” for group, “o” for others, and “a” for all, or you can use a combination of letters, similar to how you do for access rights:
$ chmod ug+rw *.php
This will make all .php files in current directory readable and writable by both user and group.
Use several permission changes within one command. Just separate them by comma.
$ chmod a-rwx,ug+rw,o+r *.php
The above will reset permissions on all .php files to readable by all and writable only by user and group.
And my favorite and most used example, which would be tricky with octal permissions is the “X”. In recursive change mode, “X” will affect executable bit only on directories. Difference by illustration:
$ chmod -R a+x /some/path
The above will add executable bit to all files and folders under /some/path.
$ chmod -R a+X /some/path
But the above will add executable bit only to folders under /some/path. The files will remain as they are.
Movie bar codes
Here is an interesting bar code idea for – compress a movie into a collection of colorful lines. Some films are easily recognizable this way, some are not. But wouldn’t it be nice if one could decompress a movie from the bar code? It would. Too bad it borders with technically impossible. Some day, maybe.
Gmail glitch – an example to follow
Once again Google demonstrates the proper way to handle issues. Due to their software update, some users temporary lost access to emails. Instead of hiding and silencing, Google published a blog post explaining the issue, as well where and when more information would be available. Not to mention that loss of service is an extremely rare occasion, and loss of data is even more so. This time, it seems, all data is recoverable from tape backups. All it takes is a little time.
Imagine the sinking feeling of logging in to your Gmail account and finding it empty. That’s what happened to 0.02% of Gmail users yesterday, and we’re very sorry. The good news is that email was never lost and we’ve restored access for many of those affected. Though it may take longer than we originally expected, we’re making good progress and things should be back to normal for everyone soon.
In times like that, keeping your users up to date is vital. All the press releases and marketing newsletters in the world won’t buy you a fraction of the trust that a simple blog post during the downtime will bring you.
LastPass XSS vulnerability found. Is it a big deal?
Via DownloadSquad I found out that a cross-site scripting (XSS) vulnerability was found in LastPass – an online password management service. The problem was reported to LastPass and they seem to have fixed it before the information went out public. What remains now is the question of how bad is this incident.
First off: don’t worry. Cardwell reported the vulnerability to LastPass before writing it up, and it has since been fixed. We’re not sure if the fix has propagated out to the Chrome and Firefox add-ons — but we have to assume that Cardwell wouldn’t have written his blog post if the vulnerability still existed.
With that said, you should still be more than a little concerned about the fundamental architecture of LastPass as an in-the-cloud password manager. While this cross-site scripting attack was fixed quickly, Cardwell thinks a similar attack “could easily happen again in future.”
[…]
It’s very hard for us to recommend LastPass as a password manager when further vulnerabilities will almost certainly be found. For the time being, you should check out KeePass, an offline password manager that, for now, is a lot more secure than LastPass.
Being a user of LastPass myself and knowing quite a few other people who use the service (some of them are even on my recommendation), I have to say that I am not pleased. I trust absolutely all of my passwords to LastPass and I rely on it being secure. Having said that, I have to point out that the world is still there. And mostly likely, it will still be there even if all those passwords get stolen and distributed all over the Internet. For sure, some people will lose some data. Some will probably lose some money. But I don’t think it can get any worse than that. Nobody will die.
More so, convenience and productivity beat security. Yes, there are a few security concerned individuals out there who would never trust their passwords to their own mother, let alone a web-based service that they have no control over. But most people aren’t like that. Most people, yours truly included, just don’t care enough. Modern world is filled with usernames and passwords and for most part people don’t care if someone else knows them or not. We only use credentials because we are forced to. Remembering all those logins and password is a tough job. Having it done by LastPass is awesome! You don’t have to remember passwords anymore. You don’t have to worry about losing them together with your laptop. You don’t have to worry about carrying the laptop with you at all times. Just save them to LastPass and you’ll be able to access them from anywhere – home, office, mobile, etc. This is so convenient that it’s almost irrelevant how many vulnerabilities will be found and exploited – LastPass still solves the hard problem for a lot of people. The only thing they have to worry about is competition that can and probably will exploit such incidents.