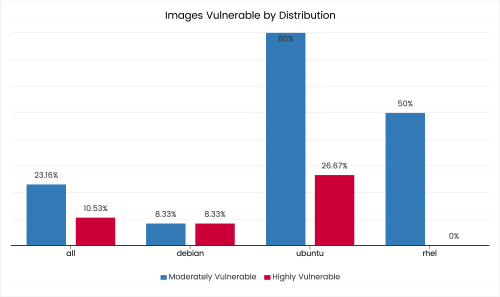
“HAProxy SNI” is pure gold! If you want to have a load balancer for HTTPS traffic, without managing SSL certificates on the said load balancer, there is a way to do so.
The approach is utilizing the Server Name Indication (SNI) extension to the TLS protocol. I knew about it and I was already using it on the web server side, but it didn’t occur to me that it’ll be utilized on the load balancer. Here’s the configuration bit:
frontend https *:443
description Incoming traffic to port 443
mode tcp
tcp-request inspect-delay 5s
tcp-request content accept if { req_ssl_hello_type 1 }
use_backend backend-ssl-foobar if { req_ssl_sni -i foobar.com }
use_backend backend-ssl-example if { req_ssl_sni -i example.com }
default_backend backend-ssl-default
The above will make HAProxy listen on port 443, and then send all traffic for foobar.com to one backend, all traffic for example.com to another backend, and the rest to the third, default backend.