Here is a nice blog post describing the important differences between array_merge_recursive() and array_replace_recursive() functions in PHP. These are often overlooked when testing new developments with simpler data structures. Troubleshooting for it later is not too obvious.
Category: Web work
These days, most of my work is very related to the online world. Building web sites, reviewing web applications, integrating with web services, coordinating people who are far away from each other, etc. Whenever I find a new tool or service or an innovative, interesting idea about working online, I share it in this category.
Yet another bit on security
Here are a couple of interesting articles from the last few days on Slashdot.
First, comes in a very non-surprising survey saying that “40 percent of organizations store admin passwords in Word documents“. Judging from my personal experiences in different companies, I’d say this number is much higher if you extend the Word documents to Excel spreadsheets and plain text files. I think pretty much every single company I’ve worked at used such common files for admin password storage (at least at some point).
“Why or why?!!!”, the security concerned among you might scream. Well, I think there are two reasons for this. The first one is that password management is complicated. There are tools that help with this, but even those are rarely easy to use. Storing the passwords in a secure, encrypted storage is one thing. But, how do you share them with just the right people? How do you trust the tool? What happens if the file gets corrupted, the software updates, the license expires, or the master password is lost? The risk of losing admin access to all your equipment and accounts is scary. On top of that, there is the issue of changing passwords (especially when people leave the company) – not a simple job if you have a variety of accounts (hardware, software, services, etc) and a lot of people who have a varying degree of access. Or automation scripts that need access to perform large scale operations. Personally, I don’t think this problem has been solved yet.
The second reason is in this other Slashdot post – “Sad Reality: It’s Cheaper To Get Hacked Than Build Strong IT Defenses“. This is very true as well. A simple firewall and a strong password policy is often more than enough for many organizations. The risks of compromise are low. In those cases where it does happen, you’d often get some script kiddie consequence like a Bitcoin mining app or affiliate links spread across your website. Both are quite easy to detect and fix. Is it worth investing hundreds of thousands in equipment and personnel to prevent this? For many companies it is not.
The fact of the matter is that a lot of people don’t really care about security or privacy on the personal level, and that then translates into the organizational mentality as well.
Just think about people leaving in all those high crime areas. Some of them think the risk is worth it – maybe then can make more money there or have a more exciting life. Some of them simply can’t afford to move anywhere. That’s very similar to the digital security, I think. Some don’t care and prefer to run the risk, saving the money on protection. Some simply can’t afford to have a decent level of security.
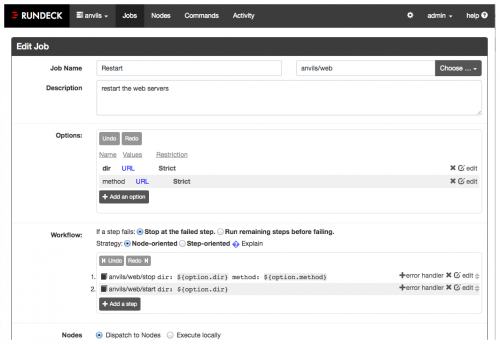
Rundeck – Job Scheduler and Runbook Automation
Rundeck is yet another one of those services that I want to get my hands on but haven’t yet got the time to. The simplest way to describe it is: cron on steroids.
Rundeck allows one to define the commands and then allow for execution on those commands manually, periodically or based on a certain trigger. Imagine, for example, a deployment command that needs to run across some servers to which you are not comfortable giving access to developers, or even non-technical users. You can create a command in Rundeck and give access to certain users to execute it, via clicking a button or two in a user friendly web interface.
A side benefit to using Rundeck versus cron are the metrics. Rundeck collects metrics like successful and failed executions, execution times, etc. So it makes it easier for you to see that certain jobs are getting progressively slower or fail on specific weekdays, etc.
The best part is that Rundeck is Open Source and self-hosted, so you don’t need to give sensitive access to some external web service.
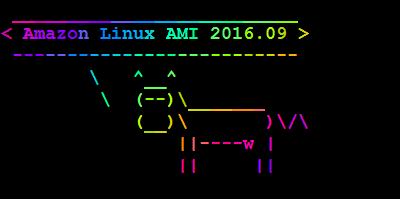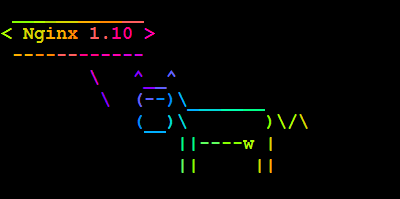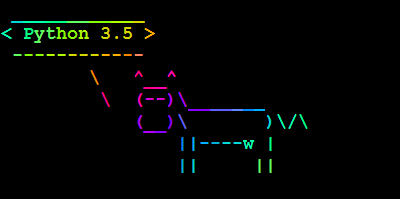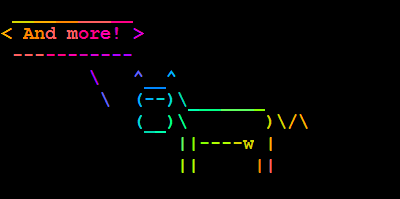
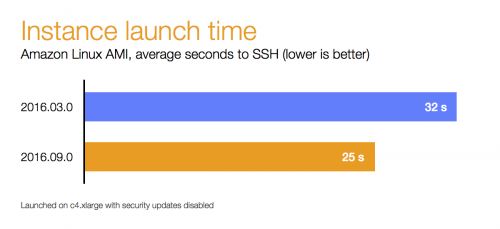
Amazon Linux AMI 2016.09
AWS Blog lets us know that Amazon Linux AMI 2016.09 is now available. It comes with a variety of updates, such as Nginx 1.10, PHP 7, and PostgreSQL 9.5 and Python 3.5. Another thing that got quite a bit of improvement is the boot time of the Amazon Linux AMI instances. Here’s a comparison chart:
Read about all the changes in the release notes.
P.S.: I’m still stuck with Amazon AMI on a few of my instances, but in general I have to remind all of you to NOT use the Amazon AMI. You’ve been warned.
Vim 8.0 Released!
The team behind the greatest text editor of all times has release the new major version – Vim 8.0. It’s the first major release in 10 years! Brief overview of the changes:
- Asynchronous I/O support, channels, JSON
- Jobs
- Timers
- Partials, Lambdas and Closures
- Packages
- New style testing
- Viminfo merged by timestamp
- GTK+ 3 support
- MS-Windows DirectX support
For a more complete list and details, have a look here.
The TL;DR summary: Vim provides a lot more power now to plugin developers, so we’ll be seeing a boost in both new functionality and old ways getting better.
Here is a mandatory Slashdot discussion with your usual Vim vs. Emacs flame.
P.S.: Emacs has recently released a major update too …