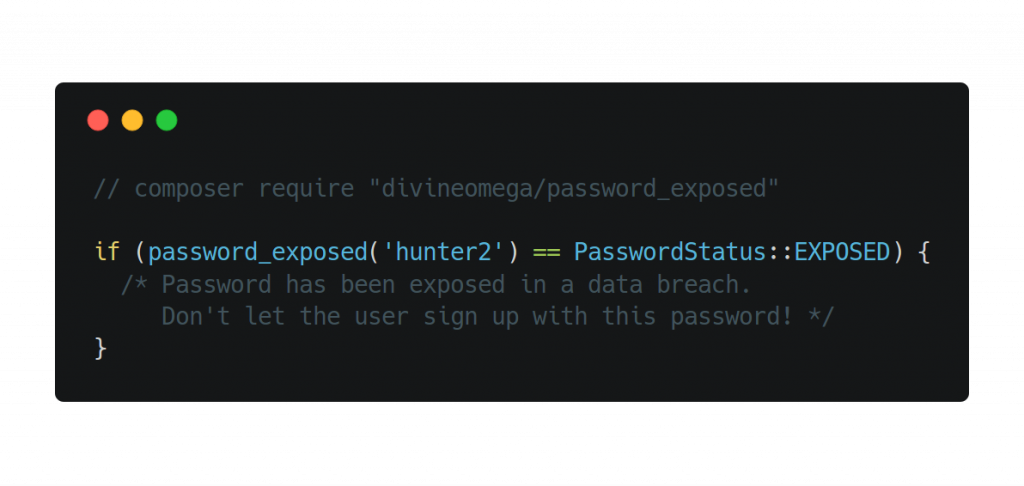
Slashdot is reporting the story:
a cluster of five, 4U servers equipped with 25 AMD Radeon GPUs communicating at 10 Gbps and 20 Gbps over Infiniband switched fabric. Gosney’s system elevates password cracking to the next level, and effectively renders even the strongest passwords protected with weaker encryption algorithms, like Microsoft’s LM and NTLM, obsolete. In a test, the researcher’s system was able to generate 348 billion NTLM password hash checks per second. That renders even the most secure password vulnerable to compute-intensive brute force and wordlist (or dictionary) attacks. A 14 character Windows XP password hashed using LM for example, would fall in just six minutes
[…]
Gosney’s cluster cranks out more than 77 million brute force attempts per second against MD5crypt.
One of my favorite comments to the story:
So now that passwords as a system is officially broken, can we please move on to something better? Something that wasn’t invented to allow soldiers standing watch in the middle of the night to tell their mates from their enemies, but is actually designed for computers?
Solutions? Well, for remote connectivity, I’ve been using SSH with key-based authentication. For the websites, Google seems to be leading the 2-way authentication progress, with a combination of password and a one-time code via SMS. These aren’t perfect, but they seem to be better than just a password.