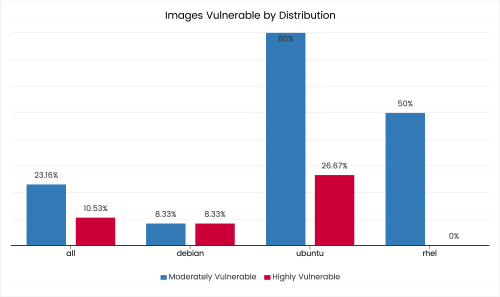
CSV, or comma-separated values, is a very common format for managing all kinds of configurations, as well data manipulation. As the linked Wikipedia page mentions, there are a few RFCs that try to standardize the format. However, I thought, there is still a lack of schema-type standard that would allow one to define a format for particular file.
Today I came across an effort that attempts to do just that – CSV Schema Language v1.1 – an unofficial draft of the language for defining and validating CSV data. This is work in progress by the Digital Preservation team at The National Archives.
Apart from the unofficial draft of the language, there is also an Open Source CSV Validator v1.1 application, written in Scala.