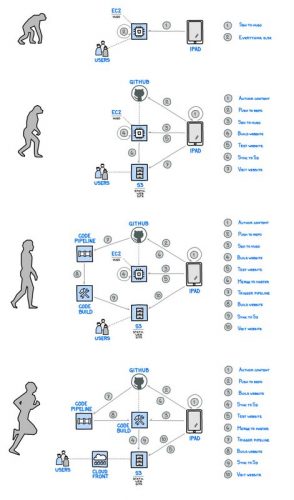
Next month I’m giving a talk on the evolution of the deployment tools and processes in the last couple of decades. This article is going along the same lines but over a much shorter period of time and only covering the static websites, not web applications. Still quite impressive as to how far and how fast the technology is changing.
Category: Sysadmin
System administration is a special are of IT. It also has a special place in my heart. It is an interesting mixture of all the other disciplines, both common across the whole industry, and at the same time unique for each person, company, and geographical location. When I have something to say or share about system administration, I use this category.
Single Sign On – You’re Probably Doing It Wrong
Arnes Blanert wrote an extensive article for the architect magazine on the subject of Single Sign On (SSO). It covers both authentication and authorization via a variety of widely and not so widely used methods, including oAuth, SAML, JSON Web Token and more.
As someone who was involved in a variety of Single Sign On implementations (see some of the posts on the subject in my blog), I wish I had an article like this in my RSS feeds much much earlier.
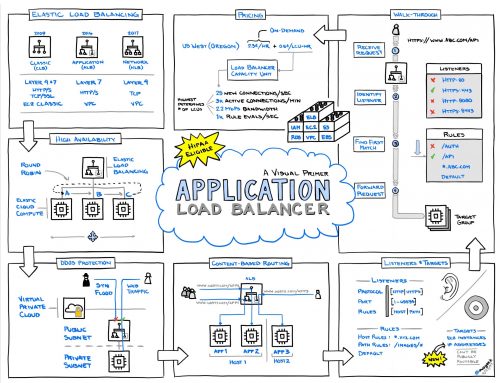
AWS Application Load Balancer
I found this visual primer to the Application Load Balancing on the Amazon AWS quite interesting. Application Load Balancing is not something I am using just yet, but it’s getting there. With more and more services and pricing schemas available from Amazon, explaining things simply is not as easy as it may seem.
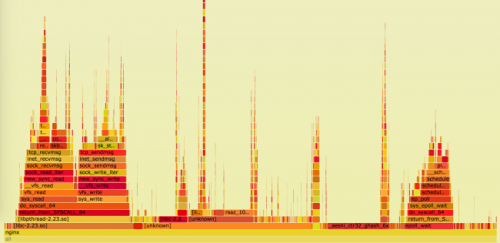
Optimizing web servers for high throughput and low latency
Dropbox Tech Blog has this in-depth article on “Optimizing web servers for high throughput and low latency“. It goes over everything from hardware and low level operating system stuff all the way up to the application level.
Great job, guys!
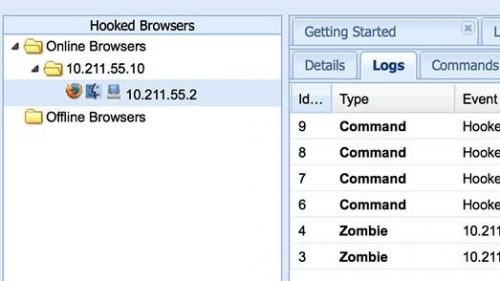
BeEF – Browser Exploitation Framework
BeEF is a browser exploitation framework.
BeEF is short for The Browser Exploitation Framework. It is a penetration testing tool that focuses on the web browser.
Amid growing concerns about web-borne attacks against clients, including mobile clients, BeEF allows the professional penetration tester to assess the actual security posture of a target environment by using client-side attack vectors. Unlike other security frameworks, BeEF looks past the hardened network perimeter and client system, and examines exploitability within the context of the one open door: the web browser. BeEF will hook one or more web browsers and use them as beachheads for launching directed command modules and further attacks against the system from within the browser context.